This post opens a series of articles describing how to use tunXten with different OpenVPN providers, whose numbers grow every day.
A word of caution – for the time being we’re not going to give a thorough review of every provider’s features, pros and cons of using one or another, or express any opinions regarding their quality of service – we just assume that one just has an account with the provider and wants to use tunXten with it instead of using their bundled client (which may not even be there).
Without further ado, let us introduce today’s provider – PrivateTunnel.
It provides access to OpenVPN servers in United States, United Kingdom, Canada and Switzerland. So, we’re gonna set up tunXten so it will be able to connect to any of these servers. To get their addresses on the internet we need to login to the provider’s web interface:
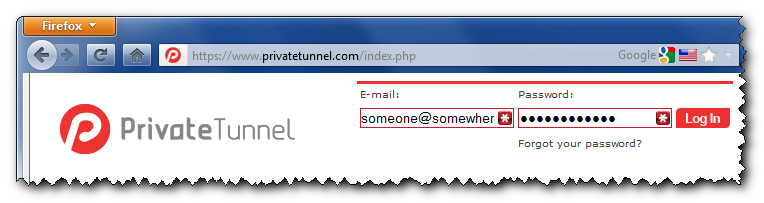
After we’re successfully in, we’ll see a combobox, which allows us to select a server we want to connect to:
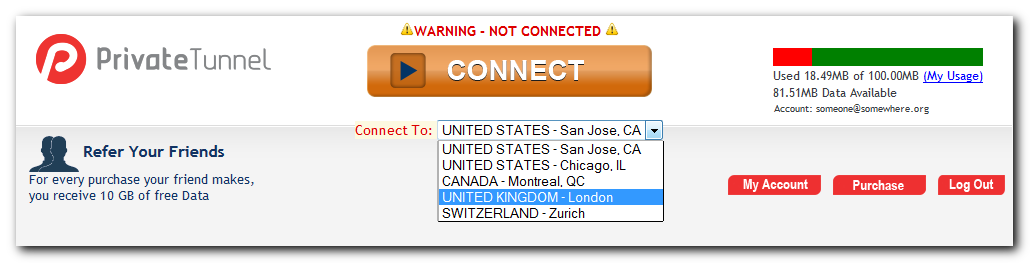
Actual addresses are hidden in the web page source, you can look them up by using “View Source” option in your browser (hit Ctrl+U in FireFox/Chrome or Alt+V+C in Internet Explorer):
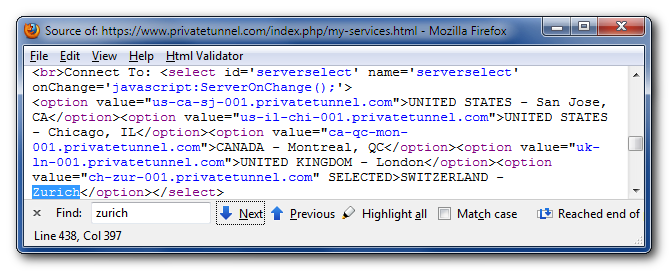
So here they are, conveniently formatted as a human-readable list:
 |
us-ca-sj-001.privatetunnel.com | United States – San Jose, CA |
 |
us-il-chi-001.privatetunnel.com | United States – Chicago, IL |
 |
ca-qc-mon-001.privatetunnel.com | Canada – Montreal, QC |
 |
uk-ln-001.privatetunnel.com | United Kingdom – London |
 |
ch-zur-001.privatetunnel.com | Switzerland – Zurich |
Now, it’s very easy to have these servers configured in tunXten – just open the Import dialog, select “I want to import my configs from OpenVPN Access Server”, enter the address of any server you like from the list above, and specify you account credentials:
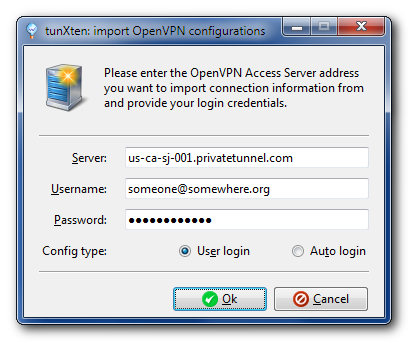
When you press the Ok button, the application automatically downloads the configuration from the remote server and makes it available for immediate use:
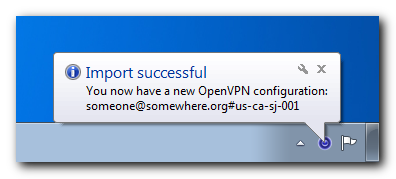
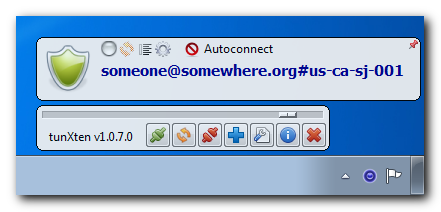
You can even import configurations from all PrivateTunnel servers to easily access any of them. Here’s what our setup looks like:
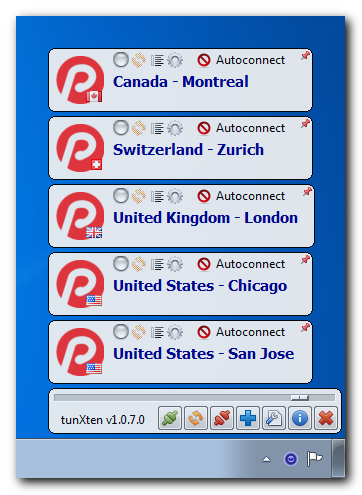
Now let’s check if it really works. First, we’ll try to connect to, say, London server:

Well, seems our connection is successfully established, let’s see now:
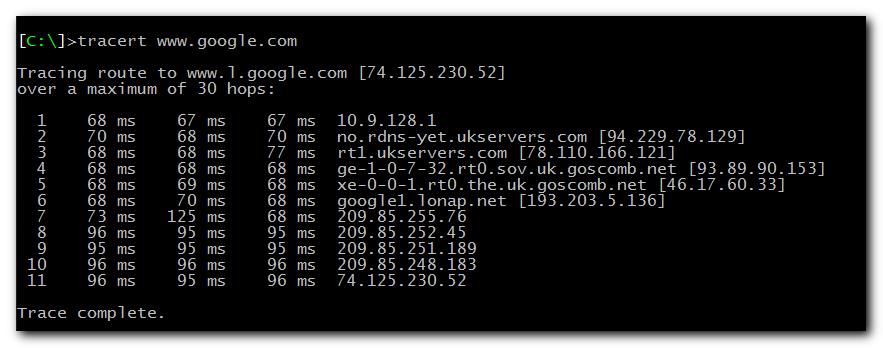
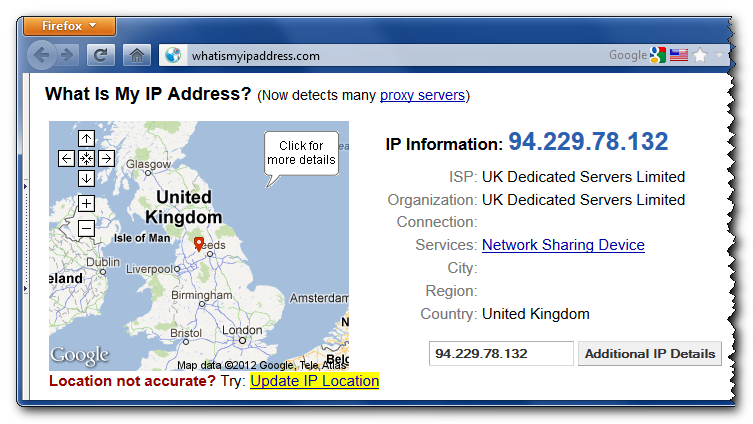
As you can see, all our network traffic now really goes through the UK server, so we can happily browse the internet feeling warm, fuzzy and secure.